21:18 CFW для PS3 Super Slim (4k) | |
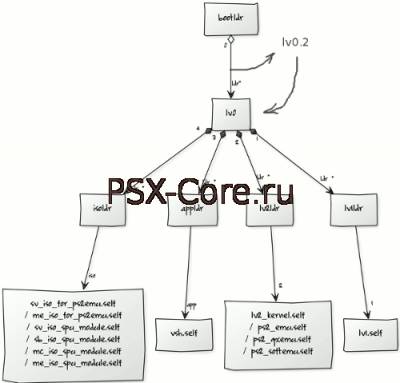
Сегодня разработчик modrobert (работающий в команде 3k3y ODE) релизнул дамп памяти PS3 4K и объявил о проекте, который направлен на реализацию Custom Firmware (CFW) для PS3 Super Slim (4K) моделей . Все подробности : https://www.eurasia.nu/modules....orum=87 Цитата modrobert After releasing 3k3y firmware v2.11 beta (with OFW 4.55 support) and losing interest in the ODE "cat & mouse" game with Sony (OFW 4.60 and 4.65), I have spent the past few weeks researching and dumping raw data in an ongoing project to extract lv0.2 keys via bootldr. Added lv0.2 to the crypto chain diagram which is how it works on PS3 Super Slim (4k). " NEW consoles only: metadata lv0.2 (signed with nonrandomfail key) is used to check lv0 integrity " As I figured it (please correct me if I'm wrong) we need the keys for lv0.2 which are held by bootldr. Some claim that bootldr is "Per Console Encrypted at factory", but I have my doubts about that, either way, as long as we can get that key on one specific console it is enough for our purpose. More on that later. What it boils down to is this (using CORE_OS data from OFW 4.65 in this test case)... Код scetool -v -d lv0.2 foo2.out scetool 0.2.9 <public build> (C) 2011-2013 by naehrwert NP local license handling (C) 2012 by flatz [*] Loaded keysets. [*] Loaded loader curves. [*] Loaded vsh curves. [*] Using keyset [lv0ldr 0x0000 00.00] [*] Error: Could not decrypt header. We need this to succeed in order to reach the final goal of installing CFW on PS3 Super Slim (4k). This is how it looks for lv0 (where we have the keys already). Код scetool -v -d lv0 foo.out scetool 0.2.9 <public build> (C) 2011-2013 by naehrwert NP local license handling (C) 2012 by flatz [*] Loaded keysets. [*] Loaded loader curves. [*] Loaded vsh curves. [*] Using keyset [lv0ldr 0x0000 00.00] [*] Header decrypted. [*] Data decrypted. [*] ELF written to foo.out. Now that's a lot better... My dumps include data from most of the PS3 4k chipsets, this was *NOT* collected by sniffing a bus (or several) in a conventional way, so even if targeted key is embedded in silicon, as long as it is processed/executed internally by any kind of microcode I might be able to catch it. At this point I don't want to reveal how the data was obtained exactly, it is a method of my own design based on several known side channel attacks. The intention is to release the method eventually.  I can clearly see the first steps during PS3 4k boot in the dumps, the syscon init of the CELL, things are a lot slower in the initial boot process, MHz rather than GHz. https://www.ps3devwiki.com/ps3/Boot_Order What I'm trying to code right now is a clever python script that will parse the raw data and test potential keys by decrypting lv0.2 in a loop. To be honest, chances are probably slim (phun intended) this will succeed even with the collected data and a clever method to test keys, but the final goal makes this project exciting no matter what the odds are! I'm really hoping this project can be a collaboration without the usual fanboy drama, Bootloader unencrypted dump 1 https://mega.co.nz/#!Ygt0k....nNd9CKo Bootloader unencrypted dump 2 https://mega.co.nz/#!05d0C....noWiylA Psx-Core.ru - активно следит за playstation# сценой,оставайтесь с нами! | |
|
| |
Похожие материалы по теме:
| Всего комментариев: 0 | |